Information security investments fall within the purview of the CFO and are included in the CFOs reports. The growing concerns about security among families school systems and legislature increased teacher and student reliance on internet accessibility.
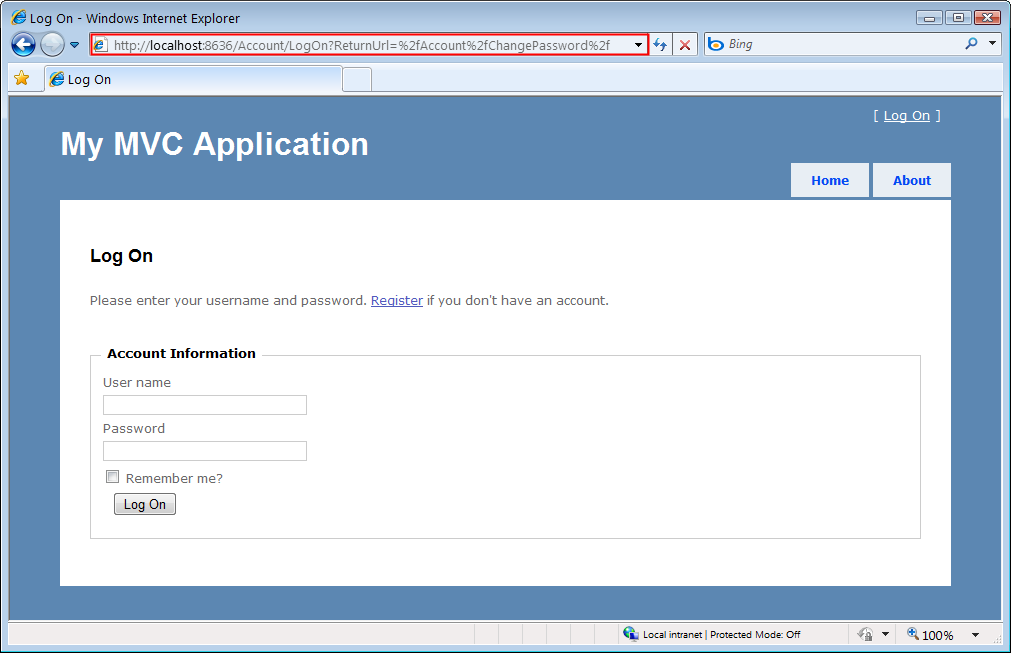
Preventing Open Redirection Attacks C Microsoft Docs

How To Fix Your Account Is Temporarily Locked On Facebook Followchain
Facebook Security Check Preventing Login And Support
Checks are done at login periodically throughout day or as an immediate response to an alert.
Security checks preventing login. If such requests are not handled correctly an attacker can launch a cross-site request forgery attack a type of attack that has made the OWASP Top 10 list of most critical web application security. Producing all checks from financial software such as QuickBooks is highly recommended. Church Background Checks for Staff and Volunteers.
Select a DBS check on the right to learn more or register for free today and discover why our pay-as-you-go DBS checks system is the solution youve been looking for. There are a number of security and safety features new to Windows Vista most of which are not available in any prior Microsoft Windows operating system release. This tutorial explains how you can prevent open redirection attacks in your ASPNET MVC applications.
That way if a hacker gains access to one account the same login info wont give them access to. Click to Tweet How to Change Your WordPress. Always use pre-numbered checks with amounts and payees typed or written in permanent ink.
Add additional security to your login process by setting up Two Factor Authentication 2FA which is also called Two Step Verification on some web services. Manage inventory and use security systems. This rule checks that there are no orphaned users.
Chief Financial Officer The CFO is the senior financial advisor to the investment review board IRB and the agency head. This tutorial discusses the changes that have been made in the AccountController in ASPNET MVC 3 and demonstrates how you can apply these changes in your existing ASPNET MVC 10 and 2 applications. We perform regular external security penetration tests throughout the year using different vendors.
The student started complaining of pain in his right big toe on the fourth day of a field training exercise FTX. This is why we incorporate many security features in our checks for preventing forgery and giving you peace of mind. The iThemes Security Pro plugin provides a real-time WordPress security dashboard that monitors security-related events on your site around the clock.
Visit one of our branches to get your replacement card instantly no wait. Locking down your WordPress admin area and login is a good way to beef up your security. During non-banking hours please contact our debit card processor CSI at 1-844-202-5333.
Unfortunately its not always possible to know if your home video surveillance camera webcam have been in the unsecured IP camera list. Report Lost or Stolen Card Please contact one of our branches during regular business hours Monday through Thursday 800 am. CBS can make your life easier.
Good usernames and passwords are key to preventing unauthorized account access. The Apple M1 chip with built-in Secure Enclave brings the same powerful security capabilities of iPhone to Mac protecting your login password automatically encrypting your data and powering file-level encryption so you stay safe. DBS checks are vital for business but they dont have to be time consuming or expensive.
The features of. Sufficient education can inculcate a security-aware culture among your API users and prevent bad actors from taking advantage of their gullibility and naivety to give out confidential information easily. Your satisfaction is guaranteed.
Security Checks Preventing Login If youre having trouble logging in to your account due to security checks youve come to the right place. Most commonly the controls being audited can be categorized to technical physical and administrative. A database user that exists on a database but has no corresponding login in the master database or as an external resource for example a Windows user is referred to as an orphaned user and it should either be removed or remapped to a valid login.
SQL Server 2012 SQL Managed Instance. Having a second factor means that an attacker cannot access an account using just a stolen password. Our Commitment to You.
Two great ways to do this is first by changing your default wp-admin login URL and also limiting login attempts. Offering recommendations for preventing problems in the future. While this improves the browsing experience it might also be a source of a security problem if a website asks the web browser to retrieve data from another website without the users consent.
Lack of elementary security features using default settings and simple passwords and security camera hack apps all result in cameras and baby monitors webcams getting hacked. In this article. As a result school cybersecurity is subject to more scrutiny than ever.
Security by obscurity can be an easy and effective way to beef up your WordPress security. The iThemes Security Dashboard is a dynamic dashboard with all your WordPress websites security activity stats in one place including brute force attacks banned users active lockouts site scan results and user security stats Pro. Lock blank checks and a signature machine if you have one in a secure place.
A shared architecture for security. Strict Mode keeps apps safe by. An information security audit is an audit on the level of information security in an organization.
Create unique usernames for your financial accounts use a different password for each site and never reuse the same username or password on multiple financial sites. Unauthorized Device and Usage Detection Access to or use of banned devices eg cell phones is detected preventing any unauthorized data capture such as via recording SMS or photos. Within the broad scope of auditing information security there are multiple types of audits multiple objectives for different audits etc.
This file can be sshauthorized_keys. This allows the attacker to login directly in a shell which would make it much easier to execute a privilege escalation. The unit medics conducted foot checks in accordance with AR 350-1 and noted mild swelling and a ruptured healing blister on top of the students toe but no.
And Friday 800 am. It is extremely important that you manually implement frequent checks of the token validity at least daily to ensure that your app is not relying on a token that has expired early for security reasons. Login pages and logins via the Mailchimp API have brute force protection.
The tests involve high-level server penetration tests in-depth testing for vulnerabilities inside the application and social engineering drills. We know check security is important to you especially in this day and age. User education in API security essentials is crucial to preventing unauthorized infiltration.
A security bug in a service running as a restricted user allows to write a file as that user. Beginning in early 2002 with Microsofts announcement of its Trustworthy Computing initiative a great deal of work has gone into making Windows Vista a more secure operating system than its predecessors. Preventing sexual predators and violent offenders from working with children and youth is our primary concern.
Please use this form to tell us about the issue youre experiencing. In this capacity the CFO is responsible for. Yet alarmingly many school systems are not sufficiently aggressive in getting ahead of cybersecurity.
In a recent edWebinar sponsored by ClassLink and co-hosted by. Track your business checks. Church background checks through Protect My Ministry are designed to help ministries implement and maintain a thorough background screening program for employees staff and volunteers.
Security Checks Preventing Facebook Login Login Information Account Loginask
:no_upscale()/cdn.vox-cdn.com/uploads/chorus_asset/file/19931158/Screenshot_20200428_152732__1_.png)
How To Set Up Two Factor Authentication On Your Online Accounts The Verge

How To Prevent Brute Force Attacks With 8 Easy Tactics Phoenixnap Kb
Logindrive Com

Security Check Preventing Login On Facebook 2020 Facebook Login Problem Bangle Tutorial For Gsm
Itprospt Com
:no_upscale()/cdn.vox-cdn.com/uploads/chorus_asset/file/22538569/Screen_Shot_2021_05_25_at_11.41.09_AM.png)
How To Set Up Two Factor Authentication On Your Online Accounts The Verge

How To Log In To Your Facebook Account Without Code Generator Make Tech Easier

